When 75% of your endpoints are mobile devices accessing corporate data, traditional security approaches simply aren’t enough anymore. Your employees are connecting from coffee shops, airports, and home offices—each connection potentially exposing your organization to sophisticated cyber threats designed specifically for mobile platforms, that's why MDM is your rock solid device management foundation but is not enough.
Mobile threat detection represents an extra security layer and fundamental shift from reactive to proactive mobile security. Unlike traditional antivirus solutions that rely on known threat signatures, or MDM's that offer more management than security capabilities, mobile threat detection tools uses artificial intelligence and behavioral analysis to identify and neutralize both known and unknown threats in real-time.
This comprehensive guide will walk you through everything you need to know about mobile threat detection—from understanding the technology to implementing it successfully across your mobile workforce.
Key takeaways
- Mobile threat detection uses AI and machine learning to identify and mitigate cyber threats targeting smartphones, tablets, and mobile devices in real-time
- 75% of devices accessing corporate data are mobile, making mobile threat detection essential for enterprise security
- Modern mobile threat detection covers three critical areas: device security, network protection, and application monitoring
- Integration with existing MDM/UEM solutions provides centralized mobile security management
- Advanced mobile threat detection prevents data breaches, ensures compliance, and enables secure BYOD policies
Understanding Mobile Threat Detection
Mobile threat detection is a cybersecurity technology that continuously monitors mobile devices for malicious activities and security vulnerabilities. Think of it as having a security guard that never sleeps, constantly watching for suspicious behavior across every aspect of your mobile device ecosystem.
Unlike traditional antivirus solutions that wait for threats to reveal themselves, mobile threat detection uses behavioral analysis and machine learning algorithms to spot anomalies before they become full-blown security incidents. The technology operates in real-time, analyzing device activities, network connections, and application behaviors simultaneously.
What makes mobile threat detection particularly powerful is its ability to protect against both known threats and zero-day attacks. While signature-based security tools can only catch threats they’ve seen before, modern MTD solutions can identify previously unknown malware by analyzing how it behaves rather than what it looks like.
On device protection ensures security even when devices are offline or disconnected from corporate networks. This is crucial for mobile workforce scenarios where employees might work in areas with limited connectivity but still need robust security measures.
Core components of Mobile Threat Detection
Modern mobile threat detection operates across three critical dimensions, each addressing specific aspects of mobile security threats.
Device security monitoring
Device security monitoring forms the foundation of any robust mobile threat defense solution. This component continuously scans device configurations, OS versions, and firmware vulnerabilities to ensure the integrity of the mobile device itself.
The system monitors for:
- Unauthorized access attempts and privilege escalation activities
- Jailbreaking, rooting, and device tampering attempts that could compromise security
- Device configuration changes that might indicate compromise
- Real-time assessment of overall device security posture
This level of monitoring is essential because compromised devices can serve as entry points for attackers to access corporate data and enterprise networks.
Network traffic analysis
Network protection represents another crucial component of mobile threat detection. Real-time monitoring of network connections and data transmission patterns helps identify threats that might bypass device-level security.
Key capabilities include:
- Detection of man-in-the-middle attacks and certificate spoofing
- Identification of connections to malicious or suspicious networks
- Protection against rogue WiFi networks and unsafe hotspots
- Analysis of data flow patterns to detect potential data theft
This is particularly important for mobile workforce scenarios where employees regularly connect to untrusted networks in public spaces.
Application behavior analysis
Application monitoring provides the third pillar of comprehensive mobile security. This component performs deep analysis of application code using advanced techniques including reverse engineering.
The system actively monitors:
- App permissions and data access patterns to identify excessive privileges
- Detection of malware, grayware, and privacy-invasive applications
- Real-time behavior analysis of installed and running apps
- Application installation sources to identify potentially risky downloads
Given that 76% of mobile attacks originate from malicious apps, this component is critical for protecting against today’s mobile threats.
How Mobile Threat Detection works
Mobile threat detection operates through a sophisticated combination of technologies working together to provide comprehensive protection for mobile endpoints.
Machine learning and AI
At the heart of modern MTD solutions, machine learning algorithms analyze billions of data points to identify threat patterns. These systems learn from each interaction, continuously improving their ability to detect both known and unknown threats.
The AI components can:
- Recognize attack patterns across different threat vectors
- Identify zero day malware through behavioral analysis
- Reduce false positives while maintaining high detection rates
- Adapt to new attack techniques automatically
Behavioral analysis
Rather than relying solely on threat signatures, behavioral analysis detects anomalies in device, network, and application activities. This approach is particularly effective against sophisticated cyberattacks that use novel techniques to avoid detection.
The system establishes baseline behaviors for:
- Normal device usage patterns
- Typical network connection behaviors
- Standard application activity levels
- Regular data access patterns
Real-Time threat intelligence
Mobile threat defense solutions leverage continuously updated threat intelligence feeds that provide information about the latest mobile threats. This real-time analysis ensures protection against emerging attack vectors as they develop.
Automated response
When threats are detected, automated response mechanisms can:
- Quarantine infected devices or malicious apps
- Block access to suspicious networks
- Alert security teams immediately
- Integrate with SIEM systems for centralized threat management
Key benefits of Mobile Threat Detection
Enhanced data protection
Mobile threat detection provides comprehensive protection for sensitive data across your entire mobile device fleet. Unlike traditional security measures that focus on perimeter defense, MTD solutions protect data wherever mobile devices travel.
Protection capabilities include:
- Prevention of data exfiltration through malicious activities
- Real-time incident response to minimize data breach impact
- Comprehensive coverage for both corporate-owned and personal mobile devices
- Advanced threat intelligence to stay ahead of emerging risks
This level of protection is essential when sensitive information regularly travels on mobile devices outside your direct control.
Improved compliance posture
Maintaining compliance becomes significantly easier with automated monitoring and enforcement of security policies across mobile device fleets. MTD solutions provide the documentation and controls necessary for regulatory requirements.
Compliance benefits:
- Automated compliance reporting for GDPR, HIPAA, and other regulations
- Continuous monitoring ensures adherence to security policies
- Documentation of security incidents and remediation actions
- Reduction of compliance violations through proactive threat prevention
Increased employee productivity
Effective mobile security shouldn’t hinder user productivity. Modern mobile threat detection solutions operate transparently, providing robust protection without impacting the user experience.
Productivity enhancements:
- Secure enablement of BYOD policies without security compromises
- Protection that works invisibly in the background
- Secure access to corporate applications from any location
- Reduced downtime from mobile security incidents
The goal is to increase productivity by enabling secure mobile work anywhere, not to restrict legitimate business activities.
Mobile Threat Detection vs. Mobile Device Management (MDM)
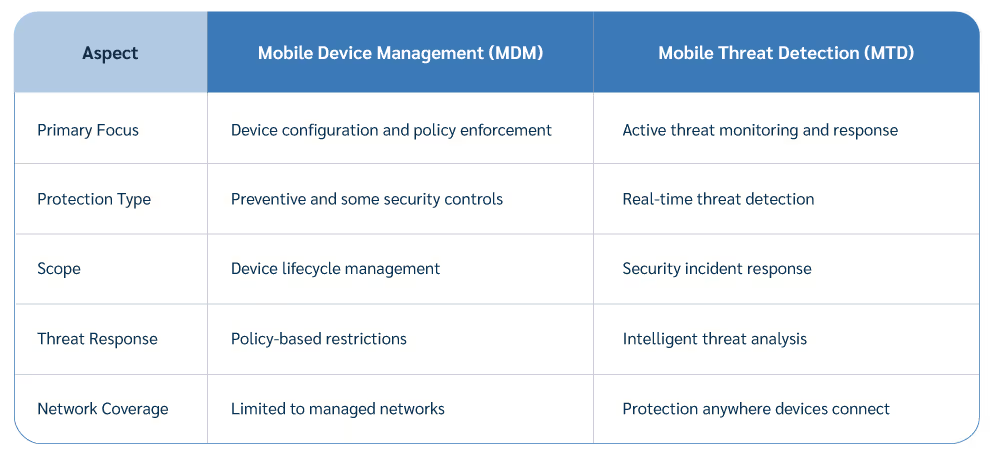
Understanding the relationship between mobile threat detection and mobile device management is crucial for building comprehensive mobile security. The MDM's are the rock-solid foundation for device management and essential security response (remote lock, wipe, encrypt), but MTD's are the crucial security layer that actively protects against a dynamic, ever-evolving threat landscape.
MDM's and MTD's are not rivals; they're the ultimate partners in crime-fighting. Think of it as a dynamic duo: MDM sets the rules, holds the keys, and MTD is watching the door and catches the bad guys trying to break-in.
Why you need both
MDM does a ton of heavy lifting, and you absolutely need it. It’s the workhorse that handles:
- Device provisioning and configuration: Getting everyone set up right, without tearing your hair out.
- Policy enforcement: Password complexity, encryption, screen lock – basically, the digital seatbelts and speed limits for your digital vehicles.
- Application management: Whitelisting, blacklisting, making sure only approved apps are lurking on company devices.
- Inventory and asset tracking: Finally knowing what’s actually out there in the wild.
- Remote lock and wipe: The nuclear option when a device goes rogue or takes an unplanned vacation.
But here’s where MDM, bless its heart, hits its limits from a pure threat perspective. MDM typically cannot detect active threats or respond to advanced security incidents in real-time.
Mobile threat detection complements MDM by adding intelligent security monitoring and response capabilities. Together, they create a comprehensive mobile security framework that addresses both preventive controls and active threat detection.
Integration benefits
When properly integrated, MDM and mobile threat detection solutions provide:
- Centralized mobile security management across device fleets
- Coordinated response to security incidents
- Comprehensive visibility into mobile device security posture
- Streamlined policy enforcement and threat response
Current mobile threat landscape
The mobile threat landscape continues evolving rapidly, with attackers developing increasingly sophisticated techniques targeting mobile workforce vulnerabilities.
Application-based threats
Malicious apps represent the largest category of mobile threats, with 76% of mobile attacks originating from applications hiding in legitimate app stores. These threats include:
- Banking trojans that steal financial credentials
- Spyware applications that monitor user activities
- Adware and grayware that compromise device performance
- Fake applications that mimic legitimate business tools
Network-based attacks
Mobile devices frequently connect to untrusted networks, creating opportunities for network-based attacks:
- Man-in-the-middle attacks on public WiFi
- Rogue access points designed to capture credentials
- DNS hijacking redirecting traffic to malicious sites
- Certificate spoofing to bypass security controls
Social engineering and phishing
With 34% of phishing attempts now targeting mobile users, social engineering has become a primary attack vector:
- SMS phishing (smishing) with malicious links
- Voice phishing (vishing) targeting mobile users
- Messaging app attacks through business communication platforms
- Mobile-optimized phishing sites designed for small screens
Emerging AI-related risks
The proliferation of AI tools introduces new data leakage risks as employees submit sensitive information to unsecured platforms without realizing the potential security implications.
Advanced features in modern Mobile Threat Detection
Today’s mobile threat defense solutions incorporate cutting-edge technologies to stay ahead of evolving threats.
AI-powered threat intelligence
Modern MTD solutions leverage artificial intelligence for pattern recognition and predictive analysis. Machine learning algorithms continuously improve detection accuracy while reducing false positives that can overwhelm security teams.
Zero-touch deployment
Touch deployment deploy capabilities enable rapid device onboarding without complicated activation steps. This is particularly valuable for organizations managing large mobile device fleets or implementing BYOD policies.
Privacy-focused architecture
Recognizing the importance of user privacy, advanced solutions perform analysis on-device without sending sensitive data to cloud servers. This approach protects user privacy while maintaining corporate security requirements.
Customizable security policies
Organizations can tailor security policies to specific requirements, device groups, or risk profiles. This flexibility ensures appropriate protection levels without unnecessary restrictions on legitimate business activities.
Zero-trust integration
Integration with zero-trust security models enables continuous verification of device trustworthiness, ensuring that mobile endpoints meet security requirements before accessing corporate resources.
Implementation best practices
Successful mobile threat detection implementation requires careful planning and attention to both technical and organizational factors.
Assessment and planning
Before deploying any MTD solution, conduct a thorough assessment of your current mobile security posture:
- Inventory all mobile devices accessing corporate data
- Identify high-risk scenarios and vulnerable access points
- Assess current security policies and compliance requirements
- Evaluate existing security infrastructure for integration opportunities
Policy development
Develop comprehensive mobile security policies that balance protection with user productivity:
- Define acceptable use for corporate and personal devices
- Establish incident response procedures for mobile security events
- Create user guidelines for safe mobile device usage
- Implement graduated response procedures based on threat severity
Integration strategy
Ensure seamless integration with existing security infrastructure:
- Connect with MDM/UEM platforms for centralized management
- Integrate with SIEM systems for comprehensive security monitoring
- Establish API connections with other security tools
- Plan for scalability as mobile device fleets grow
User education and training
End users remain a critical component of mobile security:
- Provide training on mobile security best practices
- Educate users about common mobile threats
- Establish clear communication channels for reporting security concerns
- Regular updates on emerging threats and security procedures
Future of Mobile Threat Detection
The mobile security landscape continues evolving, driven by technological advances and changing threat patterns.
Advanced AI and predictive analytics
Future mobile threat detection solutions will leverage increasingly sophisticated AI for predictive threat analysis, potentially identifying and blocking attacks before they fully materialize.
Emerging technology support
As organizations adopt new technologies, MTD solutions must expand to cover:
- 5G-specific security challenges and opportunities
- IoT device integration with mobile endpoints
- Edge computing security requirements
- Extended reality (XR) applications and devices
Privacy-preserving technologies
Development of quantum-resistant encryption and zero-knowledge architectures will enable stronger security while better protecting user privacy.
Expanded threat coverage
Future solutions will address new attack vectors including:
- AI-powered social engineering attacks
- Deepfake-based fraud targeting mobile users
- Supply chain attacks through mobile applications
- Cross-platform attack techniques spanning multiple device types
Selecting the right mobile Threat Detection Solution
Choosing the appropriate MTD solution requires careful evaluation of multiple factors aligned with your organization’s specific needs.
Detection capabilities
Evaluate the solution’s ability to detect various threat types:
- Accuracy rates for different threat categories
- False positive rates and their impact on operations
- Zero-day detection capabilities through behavioral analysis
- Coverage scope across device, network, and application threats
Integration and compatibility
Assess how well the solution integrates with existing infrastructure:
- MDM/UEM platform compatibility for unified management
- SIEM integration capabilities for centralized monitoring
- API availability for custom integrations
- Cloud, on-premise, and hybrid deployment options
User experience
Consider the impact on end users and device performance:
- Transparent operation without user disruption
- Battery life impact and device performance
- User interface design for security notifications
- Privacy protection and data handling practices
Vendor evaluation
Research vendor capabilities and track record:
- Threat intelligence quality and research capabilities
- Industry expertise and customer references
- Support and maintenance offerings
- Roadmap alignment with your future needs
Total cost of ownership
Calculate comprehensive costs including:
- Licensing fees for different deployment scales
- Implementation and training costs
- Ongoing maintenance and support expenses
- Integration effort with existing systems
FAQ
What is the difference between mobile threat detection and mobile antivirus?
Mobile threat detection uses behavioral analysis and machine learning to identify threats, while traditional antivirus relies primarily on signature-based detection. MTD solutions provide real-time monitoring of device, network, and application activities, enabling detection of zero-day attacks and unknown threats that signature-based tools would miss. Additionally, mobile threat detection integrates with enterprise security infrastructure for centralized management, making it more suitable for organizational deployments.
How does mobile threat detection protect user privacy?
Modern MTD solutions perform analysis on-device without sending personal data to cloud servers. Privacy-focused architectures separate corporate security monitoring from personal device activities, allowing users to maintain control over personal applications and data while ensuring corporate security. GDPR and privacy regulation compliance is built into solution design and deployment, with clear boundaries between personal and corporate data protection.
Can mobile threat detection work offline?
Yes, advanced mobile threat detection solutions provide on-device protection that works without internet connectivity. Local threat analysis engines continue monitoring device activities when offline, ensuring continuous protection regardless of network availability. Threat intelligence updates synchronize when connectivity is restored, and critical security actions can be taken immediately without cloud dependency.
What types of threats can mobile threat detection identify?
Mobile threat detection can identify a comprehensive range of threats including malicious applications (malware, spyware, adware), network-based attacks (man-in-the-middle, certificate spoofing), mobile phishing attempts through SMS and messaging apps, device compromise indicators (jailbreaking, rooting, tampering), and data exfiltration attempts. The technology is particularly effective at detecting unknown threats through behavioral analysis rather than relying solely on known threat signatures.
How quickly can mobile threat detection respond to threats?
Real-time threat detection provides immediate identification of malicious activities, with automated response mechanisms capable of quarantining threats within seconds of detection. Security teams receive instant alerts for critical threats requiring manual intervention, while machine learning algorithms continuously improve response speed and accuracy. The combination of automated response and human oversight ensures both rapid threat neutralization and appropriate escalation when necessary.
Mobile threat detection has evolved from a luxury to a necessity in today’s mobile-first business environment. As cyber threats become more sophisticated and mobile devices handle increasingly sensitive corporate data, organizations need proactive security solutions that can adapt and respond in real-time.
The key to successful mobile threat detection implementation lies in understanding that it’s not just about technology—it’s about enabling your workforce to be productive anywhere while keeping your data secure. By combining advanced threat detection with user-friendly deployment and transparent operation, organizations can achieve the balance between security and productivity that modern business demands.
Whether you’re just beginning to evaluate mobile threat detection or looking to upgrade existing solutions, the investment in comprehensive mobile security pays dividends through reduced risk, improved compliance, and increased employee productivity. The mobile world isn’t slowing down, and neither should your security strategy.